The switch from 1080p to 4K resolution in home entertainment has generated discussions among fans and casual watchers alike. The…
Read More »Tech
Modern gadgets operate in standby mode to save energy. Devices may be set into standby mode to be ready to…
Read More »You may be in a quandary of the usb types that are available for your purchase, in particular, the two…
Read More »The best USB-C to HDMI cable can be determined by considering certain factors. These can help you make a firm…
Read More »As technology evolves rapidly, the need for adaptable and future-proof solutions becomes more critical. Enter Anker’s docking stations, which not…
Read More »Choosing the right security camera for your home can be challenging with the wide array of options available. The eufy…
Read More »Having wired security cameras may have piqued your interest and now, you are thinking of buying one yourself. Being wired…
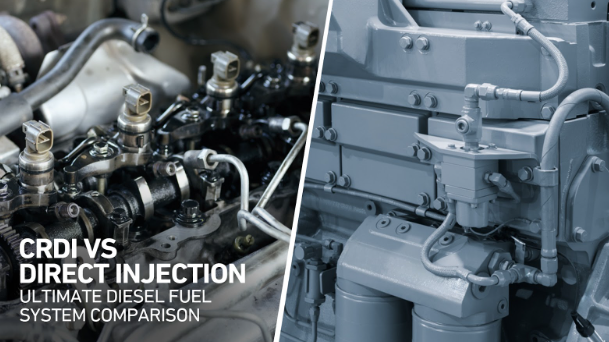
Read More »Ever since its invention in 1897 by Rudolph Diesel, diesel engines have seen numerous improvements over the years. Right from…
Read More »When deciding what is best regarding communication, especially in remote areas, it may be tricky to choose between a walkie-talkie…
Read More »Electrical hazard labeling is an effective way to enhance safety measures that help prevent electrical risks that are a source…
Read More »